
I. Targeted Entities
ConnectWise ScreenConnect customers
II. Introduction
A critical authentication bypass has been discovered in ConnectWise’s ScreenConnect, a software for remote desktop access. This exploit potentially allows attackers access to confidential information and critical systems without needing the proper credentials. Once authenticated via the authentication bypass, attackers can leverage a path-traversal vulnerability to potentially execute remote code inside critical systems.
III. Additional Background Information
On February 19, 2024, ConnectWise released a Threat Advisory for patching multiple vulnerabilities discovered in the company’s ScreenConnect software. ScreenConnect is a remote desktop and access software that can be used for direct connections to desktops, mobile devices, and more. The vulnerabilities, CVE-2024-1709 and CVE-2024-1708, were first reported on February 13th. These vulnerabilities have been classified as significantly exploitable with CVE-2024-1709 receiving a 10.0 critical base score and CVE-2024-1708 receiving an 8.4 high base score by NIST.
The first vulnerability, CVE-2024-1709, involves authentication bypass, which is directly related to CWE-288 – Authentication Bypass Using an Alternate Path or Channel. A flaw was found in a text file named “SetupWizard.aspx”, which has the functionality of setting up the administrative user and installing a license for the system. In unpatched versions, this setup file can be accessed even after the initial setup is completed. This is accomplished by adding additional components after the legitimate URL to SetupWizard.aspx (/SetupWizard.aspx/[anything]) and exploiting how the .NET framework handles URL paths. The code inside the text file does not check if the ScreenConnect instance setup has already been completed, making it possible for anyone to access the setup wizard and overwrite the internal user database, effectively gaining administrative access (Poudel, 2024).
The second vulnerability, CVE-2024-1708, is related to CWE-22 – Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’). Although it is considered less severe as it is unlocked by CVE-2024-1079, it must not be underestimated (Team Huntress, 2024). This vulnerability involves manipulating ZIP file paths when extracting its contents. Attackers can then modify these contents and execute malicious code (Poudel, 2024). To do this, a malicious actor needs to have both administrative credentials and create a malicious extension inside C:Program Files (x86)ScreenConnectApp_Extensions to write files anywhere within the folder (Team Huntress, 2024). Team Huntress showed that this ZipSlip attack was not necessary, as malicious actors can run code by accessing a ScreenConnect feature called “Extensions”. This could potentially go easily unnoticed in a system since no other extensions need to be installed (Team Huntress, 2024).
ConnectWise released a patched version of ScreenConnect on February 21st, 2024, and recommends updating all 23.9.7 and earlier versions to 23.9.8 (ConnectWise, 2024). As of today, February 22nd, 2024, 3,800 instances of ScreenConnect have been found vulnerable, and need to be updated to the latest version in order to prevent malicious actors from accessing the ScreenConnect environment. ConnectWise added that Cloud instances were automatically patched, while On-Prem partners need to install all the required updates manually to remediate against both vulnerabilities (ConnectWise).
V. MITRE ATT&CK
- T1190 – Exploit Public-Facing Applications
Adversaries may attempt to exploit a weakness in an Internet-facing host or system to initially access a network. The weakness in the system can be a software bug, a temporary glitch, or a misconfiguration. Adversaries exploited CVE-2023-3519 to implant a webshell on the organization’s NetScaler ADC appliance.
- T1068 – Exploitation for Privilege Escalation
Adversaries may exploit software vulnerabilities to elevate privileges. Exploitation of a software vulnerability occurs when an adversary takes advantage of a programming error in a program, service, or within the operating system software or kernel itself to execute adversary-controlled code.
- T1105 – Ingress Tool Transfer
Adversaries may transfer tools or other files from an external system into a compromised environment. Tools or files may be copied from an external adversary-controlled system to the victim network through the command-and-control channel or through alternate protocols such as ftp. Once present, adversaries may also transfer/spread tools between victim devices within a compromised environment.
- T1136 – Create Account
Adversaries may create an account to maintain access to victim systems. With a sufficient level of access, creating such accounts may be used to establish secondary credentialed access that does not require persistent remote access tools to be deployed on the system.
- T1203 – Exploitation for Client Execution
Adversaries may exploit software vulnerabilities in client applications to execute code. Vulnerabilities can exist in software due to insecure coding practices that can lead to unanticipated behavior. Adversaries can take advantage of certain vulnerabilities through targeted exploitation for the purpose of arbitrary code execution.
VI. Recommendations
- On-premise users should immediately upgrade to ScreenConnect version 23.9.8 or later as these versions patch the vulnerabilities.
- Refer to ConnectWise’s guide for upgrading to the newest software version: Upgrade an on-premises installation.
- Refer to this link to download the newest ScreenConnect patches: ScreenConnect Patch Download
- It is important to keep all software up to date with the latest patches.
- Check your system for indicators of compromise in the last 30 days.
VII. IOCs (Indicators of Compromise)
CVE-2024-1709
| Type | Indicator |
|---|---|
| Threat Actor IP Address |
155[.]133[.]5[.]15 |
| Threat Actor IP Address |
155[.]133[.]5[.]14 |
| Threat Actor IP Address |
118[.]69[.]65[.]60 |
| Setup Wizard Sigma Rule | Sigma Rule Github Page |
| ScreenConnect New User Database XML File Modification Sigma Rule | Sigma Rule Github Page |
| Setup Wizard YARA Rule | YARA Rule Github Page |
CVE-2024-1708
| Type | Indicator |
|---|---|
| Threat Actor IP Address |
155[.]133[.]5[.]15 |
| Threat Actor IP Address |
155[.]133[.]5[.]14 |
| Threat Actor IP Address |
118[.]69[.]65[.]60 |
| App Extensions Directory Sigma Rule | Sigma Rule Github Page |
VII. Additional OSINT Information
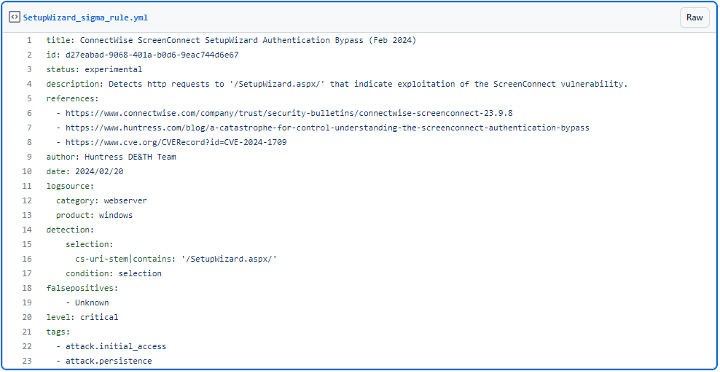
Sigma rule for detecting requests made to the Setup Wizard with trailing paths (Huntress).
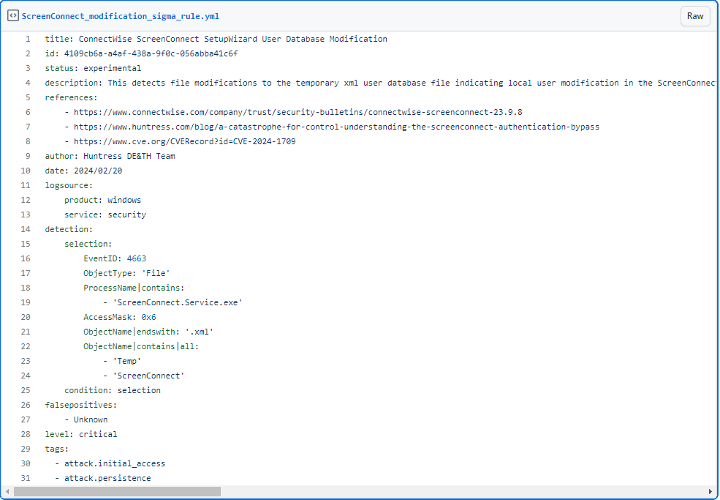
Sigma rule for detecting the ScreenConnect server writing to a temporary XML file (Huntress).
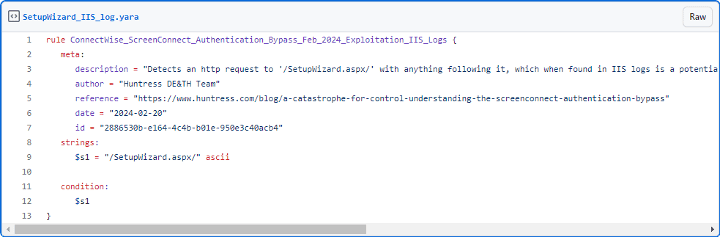
Setup Wizard YARA Rule for detecting Internet Information Services (IIS) log entries in reference to the SetupWizard (Huntress).
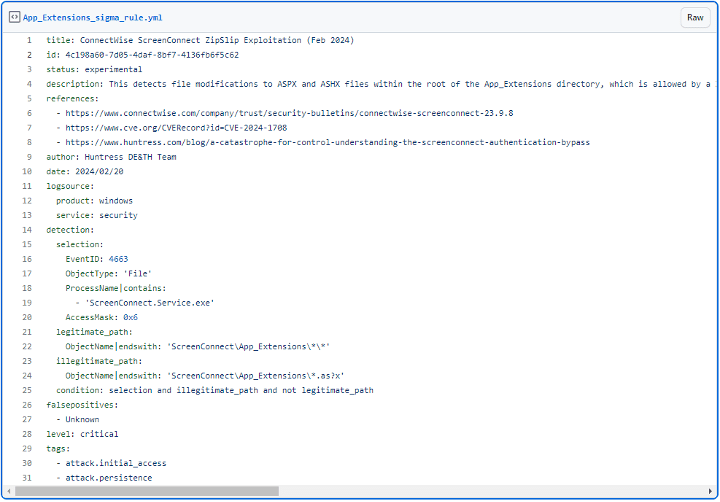
Sigma rule that alerts file modifications in the App_Extensions root directory (Huntress).
VIII. References
CVE-2024-1709. NIST. (n.d.-b). https://nvd.nist.gov/vuln/detail/CVE-2024-1709
CVE-2024-1708. NIST. (n.d.-a). https://nvd.nist.gov/vuln/detail/CVE-2024-1708
ConnectWise ScreenConnect 23.9.8 security fix. ConnectWise. (2024, February 19). https://www.connectwise.com/company/trust/security-bulletins/connectwise-screenconnect-23.9.8
Detection guidance for ConnectWise CWE-288. Huntress. (2024a, February 20). https://www.huntress.com/blog/detection-guidance-for-connectwise-cwe-288-2
Understanding the ConnectWise screenconnect CVE-2024-1709 & CVE-2024-1708: Huntress blog. Huntress. (2024, February 21). https://www.huntress.com/blog/a-catastrophe-for-control-understanding-the-screenconnect-authentication-bypass
Mitre ATT&CK®. MITRE. (n.d.). https://attack.mitre.org/
Poudel, S. (2024, February 22). Unveiling the ScreenConnect authentication bypass (CVE-2024-1709 & CVE-2024-1708). Logpoint. https://www.logpoint.com/en/blog/emerging-threats/screenconnect-authentication-bypass/
Threat Advisory created by The Cyber Florida Security Operations Center. Contributing Security Analysts: Alessandro Lovadina, Benjamin Price
