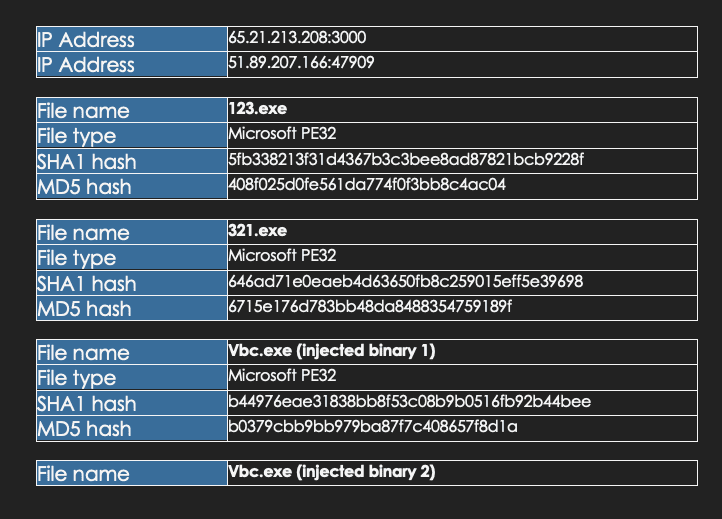
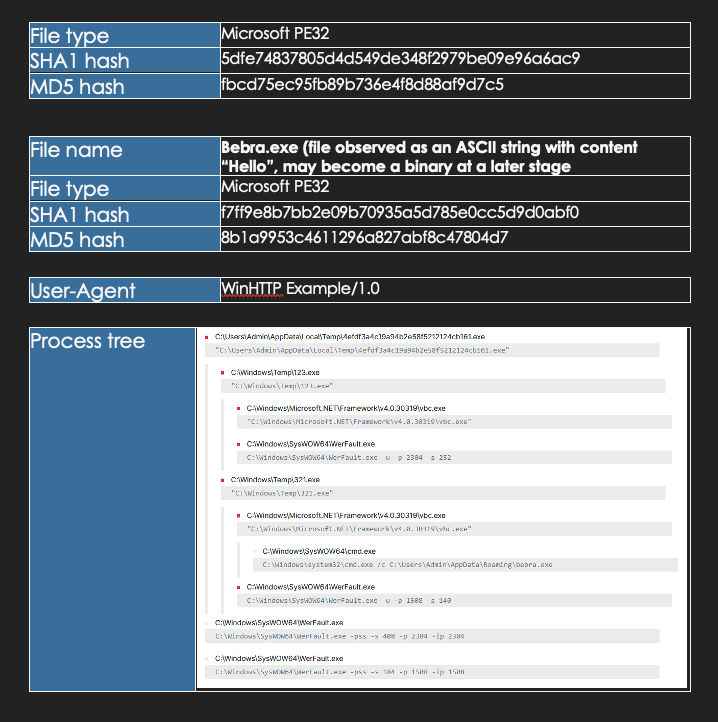
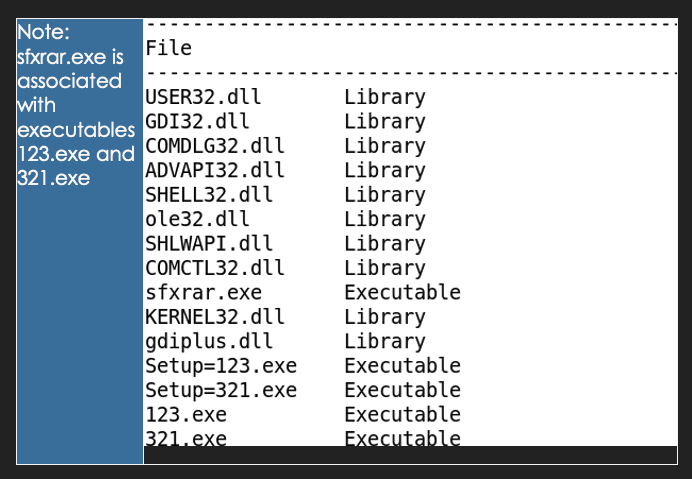
I. Targeted Entities
II. Introduction
Multiple vulnerabilities have recently been identified in Fortinet products. These products are designed to provide network security solutions that offer protection from constantly emerging threats to your network, data, and users. (Fortiguard 2023)
III. Background Information
Fortinet has recently revealed a highly severe vulnerability, marked as “Critical,” that affects both FortiOS and FortiProxy. This flaw permits an attacker who has not been authenticated to run arbitrary code or conduct a denial-of-service (DoS) attack on the graphical user interface (GUI) of the affected systems by employing specially designed requests. (Toulas, 2023)
The vulnerability is recognized as CVE-2023-25610 and has obtained a CVSS v3 score of 9.3, which is classified as critical. A buffer underflow vulnerability like this occurs when a program attempts to read more data from a memory buffer than is available. This leads to accessing adjacent memory locations, potentially resulting in unstable behavior or system crashes. Fortinet’s telemetry data revealed no evidence that threat actors exploited the vulnerability in real-world attacks. (Multiple Vulnerabilities in Fortinet Products Could Allow for Arbitrary Code 2023)
According to Fortinet’s security bulletin, there are fifty device models that are not affected by the arbitrary code execution aspect of the vulnerability. However, these same models are still vulnerable to the denial-of-service part, even if they are running a vulnerable version of FortiOS. (Toulas, 2023)
Affected Products:
FortiOS version 7.2.0 through 7.2.3
FortiOS version 7.0.0 through 7.0.9
FortiOS version 6.4.0 through 6.4.11
FortiOS version 6.2.0 through 6.2.12
FortiOS 6.0 all versions
FortiProxy version 7.2.0 through 7.2.2
FortiProxy version 7.0.0 through 7.0.8
FortiProxy version 2.0.0 through 2.0.12
FortiProxy 1.2 all versions
FortiProxy 1.1 all versions
For those who cannot apply the updates immediately, Fortinet recommends either disabling the HTTP/HTTPS administrative interface or restricting the IP addresses that can access it remotely. Instructions on how to implement these workarounds, which also apply to non-default port usage, are provided in the security advisory.
Threat actors are actively searching for critical-severity vulnerabilities in Fortinet products, particularly those that do not require authentication to exploit. These vulnerabilities provide attackers with a means of gaining initial access to corporate networks. As a result, it is critical to quickly address this vulnerability. (Toulas, 2023)
IV. Updated Information and CVE’s in Relation with Observed Fortinet Vulnerabilities
According to an article published by Bleeping Computer on March 15, 2023, a new vulnerability in FortiOS, the operating system of Fortinet firewalls, is being actively exploited in the wild to attack government networks. The vulnerability, designated as CVE-2023-41328, is a zero-day vulnerability, meaning that it was unknown to the vendor and the public before being exploited by threat actors.
The attack appears to be highly targeted, aimed at specific government agencies. The attackers used the vulnerability to gain access to the victim’s network and install a backdoor that allowed them to exfiltrate data and execute commands on the compromised systems.
Fortinet has released a patch for the vulnerability and is urging all customers to update their systems immediately. The company has also stated that it is working closely with law enforcement and other relevant authorities to investigate the attacks and identify the perpetrators.
- CVE-2022-41328 – FortiOS – Path traversal in execute command
- CVE-2022-39951 – FortiWeb – command injection in webserver: An improper neutralization of special elements used in an OS command vulnerability in FortiWeb may allow authenticated users to execute unauthorized code or commands via specifically crafted HTTP requests.
- CVE-2022-39953 – FortiNAC – Multiple privilege escalation via sudo command: An improper privilege management vulnerability in FortiNAC may allow a low privilege local user with shell access to execute arbitrary commands as root.
- CVE-2022-40676 – FortiNAC – Multiple Reflected XSS: An improper neutralization of input during web page generation in FortiNAC may allow an authenticated user to perform an XSS attack via crafted HTTP requests.
- CVE-2023-25605 – FortiSOAR – Improper Authorization in request headers: An improper access control vulnerability in FortiSOAR’s playbook component may allow an attacker authenticated on the administrative interface to perform unauthorized actions via crafted HTTP requests.
- CVE-2022-42476 – FortiOS / FortiProxy – Path traversal vulnerability allows VDOM escaping: A relative path traversal vulnerability in FortiOS and FortiProxy may allow privileged VDOM administrators to escalate their privileges to super admin of the box via crafted CLI requests.
V. MITRE ATT&CK
- T1190 – Exploit Public-Facing Application
Adversaries may attempt to take advantage of a weakness in an Internet-facing computer or program using software, data, or commands to cause unintended or unanticipated behavior. The weakness in the system can be a bug, a glitch, or a design vulnerability. These applications are often websites, but can include databases (like SQL), standard services (like SMB or SSH), network device administration and management protocols (like SNMP and Smart Install), and any other applications with Internet accessible open sockets, such as web servers and related services.
- T1499 – Endpoint Denial-Of-Service
Adversaries may perform Endpoint Denial of Service (DoS) attacks to degrade or block the availability of services to users. Endpoint DoS can be performed by exhausting the system resources those services are hosted on or exploiting the system to cause a persistent crash condition.
V. Recommendations From the Center for Internet Security (MS-ISAC)
- Safeguard 7.1: Establish and Maintain a Vulnerability Management Process:
Establish and maintain a documented vulnerability management process for enterprise assets. Review and update documentation annually, or when significant enterprise changes occur that could impact this Safeguard.
- Safeguard 7.2: Establish and Maintain a Remediation Process:
Establish and maintain a risk-based remediation strategy documented in a remediation process, with monthly, or more frequent, reviews.
- Safeguard 7.3: Perform Automated Operating System Patch Management:
Perform operating system updates on enterprise assets through automated patch management on a monthly, or more frequent, basis.
- Safeguard 7.4: Perform Automated Application Patch Management:
Perform application updates on enterprise assets through automated patch management on a monthly, or more frequent, basis.
- Safeguard 7.6: Perform Automated Vulnerability Scans of Externally Exposed Enterprise Assets:
Perform automated vulnerability scans of externally-exposed enterprise assets using a SCAP-compliant vulnerability scanning tool. Perform scans on a monthly, or more frequent, basis.
- Safeguard 7.7: Remediate Detected Vulnerabilities:
Remediate detected vulnerabilities in software through processes and tooling on a monthly, or more frequent, basis, based on the remediation process.
- Safeguard 12.1: Ensure Network Infrastructure is Up-to-Date:
Ensure network infrastructure is kept up-to-date. Example implementations include running the latest stable release of software and/or using currently supported network-as-a-service (NaaS) offerings. Review software versions monthly, or more frequently, to verify software support.
- Safeguard 18.1: Establish and Maintain a Penetration Testing Program:
Establish and maintain a penetration testing program appropriate to the size, complexity, and maturity of the enterprise. Penetration testing program characteristics include scope, such as network, web application, Application Programming Interface (API), hosted services, and physical premise controls; frequency; limitations, such as acceptable hours, and excluded attack types; point of contact information; remediation, such as how findings will be routed internally; and retrospective requirements.
- Safeguard 18.2: Perform Periodic External Penetration Tests:
Perform periodic external penetration tests based on program requirements, no less than annually. External penetration testing must include enterprise and environmental reconnaissance to detect exploitable information. Penetration testing requires specialized skills and experience and must be conducted through a qualified party. The testing may be clear box or opaque box.
- Safeguard 18.3: Remediate Penetration Test Findings:
Remediate penetration test findings based on the enterprise’s policy for remediation scope and prioritization. Vulnerability scanning is used to find potentially exploitable software vulnerabilities to remediate them. (M1016: Vulnerability Scanning)
- Safeguard 16.13: Conduct Application Penetration Testing:
Conduct application penetration testing. For critical applications, authenticated penetration testing is better suited to finding business logic vulnerabilities than code scanning and automated security testing. Penetration testing relies on the skill of the tester to manually manipulate an application as an authenticated and unauthenticated user.
- Apply the Principle of Least Privilege to all systems and services. Run all software as a non-privileged user (one without administrative privileges) to diminish the effects of a successful attack. (M1026: Privileged Account Management)
- Safeguard 4.7: Manage Default Accounts on Enterprise Assets and Software:
Manage default accounts on enterprise assets and software, such as root, administrator, and other pre-configured vendor accounts. Example implementations can include disabling default accounts or making them unusable.
- Safeguard 5.4: Restrict Administrator Privileges to Dedicated Administrator Accounts:
Restrict administrator privileges to dedicated administrator accounts on enterprise assets. Conduct general computing activities, such as internet browsing, email, and productivity suite use, from the user’s primary, non-privileged account.
- Safeguard 5.5: Establish and Maintain an Inventory of Service Accounts:
Establish and maintain an inventory of service accounts. The inventory, at a minimum, must contain department owner, review date, and purpose. Perform service account reviews to validate that all active accounts are authorized, on a recurring schedule at a minimum quarterly, or more frequently.
- Safeguard 6.8: Define and Maintain Role-Based Access Control:
Define and maintain role-based access control, through determining and documenting the access rights necessary for each role within the enterprise to successfully carry out its assigned duties. Perform access control reviews of enterprise assets to validate that all privileges are authorized, on a recurring schedule at a minimum annually, or more frequently.
- Architect sections of the network to isolate critical systems, functions, or resources. Use physical and logical segmentation to prevent access to potentially sensitive systems and information. Use a DMZ to contain any internet-facing services that should not be exposed from the internal network. Configure separate virtual private cloud (VPC) instances to isolate critical cloud systems. (M1030: Network Segmentation)
- Safeguard 12.2: Establish and Maintain a Secure Network Architecture:
Establish and maintain a secure network architecture. A secure network architecture must address segmentation, least privilege, and availability, at a minimum. Restrict execution of code to a virtual environment on or in transit to an endpoint system. (M1048: Application Isolation and Sandboxing)
- Safeguard 16.8: Separate Production and Non-Production Systems:
Maintain separate environments for production and non-production systems. Use capabilities to detect and block conditions that may lead to or be indicative of a software exploit occurring. (M1050: Exploit Protection)
- Safeguard 10.5: Enable Anti-Exploitation Features:
Enable anti-exploitation features on enterprise assets and software, where possible, such as Microsoft® Data Execution Prevention (DEP), Windows® Defender Exploit Guard (WDEG), or Apple® System Integrity Protection (SIP) and Gatekeeper™.
- Restrict use of certain websites, block downloads/attachments, block Javascript, restrict browser extensions, etc. (M1021: Restrict Web-Based Content)
- Safeguard 9.2: Use DNS Filtering Services:
Use DNS filtering services on all enterprise assets to block access to known malicious domains.
- Safeguard 9.3: Maintain and Enforce Network-Based URL Filters:
Enforce and update network-based URL filters to limit an enterprise asset from connecting to potentially malicious or unapproved websites. Example implementations include category-based filtering, reputation-based filtering, or using block lists. Enforce filters for all enterprise assets.
- Safeguard 9.6: Block Unnecessary File Types:
Block unnecessary file types attempting to enter the enterprise’s email gateway. Inform and educate users regarding the threats posed by hypertext links contained in emails or attachments especially from un-trusted sources. Remind users not to visit un-trusted websites or follow links provided by unknown or un-trusted sources. (M1017: User Training)
- Safeguard 14.1: Establish and Maintain a Security Awareness Program:
Establish and maintain a security awareness program. The purpose of a security awareness program is to educate the enterprise’s workforce on how to interact with enterprise assets and data in a secure manner. Conduct training at hire and, at a minimum, annually. Review and update content annually, or when significant enterprise changes occur that could impact this Safeguard.
- Safeguard 14.2: Train Workforce Members to Recognize Social Engineering Attacks:
Train workforce members to recognize social engineering attacks, such as phishing, pre-texting, and tailgating.
VII. References
- Toulas, B. (2023, March 8). Fortinet warns of New Critical unauthenticated RCE vulnerability. BleepingComputer. Retrieved March 13, 2023, from https://www.bleepingcomputer.com/news/security/fortinet-warns-of-new-critical-unauthenticated-rce-vulnerability/
- Fortiguard. FortiGuard. (n.d.). Retrieved March 13, 2023, from https://www.fortiguard.com/psirt-monthly-advisory/march-2023-vulnerability-advisories
- Fortiguard. FortiGuard. (n.d.). Retrieved March 13, 2023, from https://www.fortiguard.com/psirt/FG-IR-23-001
- Endpoint denial of service. Endpoint Denial of Service, Technique T1499 – Enterprise | MITRE ATT&CK®. (n.d.). Retrieved March 13, 2023, from https://attack.mitre.org/techniques/T1499/
- Exploit public-facing application. Exploit Public-Facing Application, Technique T1190 – Enterprise | MITRE ATT&CK®. (n.d.). Retrieved March 13, 2023, from https://attack.mitre.org/techniques/T1190/
- Recorded future: Securing our world with intelligence. Recorded Future: Securing Our World With Intelligence. (n.d.). Retrieved March 13, 2023, from https://www.recordedfuture.com/
- (2023, March 8). MS-ISAC CYBERSECURITY ADVISORY – Multiple Vulnerabilities in Fortinet Products Could Allow for Arbitrary Code Execution – PATCH NOW – TLP: CLEAR.
Threat Advisory created by The Cyber Florida Security Operations Center. Contributing Security Analysts: EJ Bulut