Scattered Spider Threat Report

I. Introduction
Scattered Spider is a large and loosely affiliated cybercrime group also referred to as UNC3944 or Octo Tempest. This group is made up of teens and young adults who primarily target companies in the U.S. and U.K. for financial gain (CISA, 2025).
Their attacks are heavily reliant on social engineering. Common tactics include bombarding employees with repeated MFA prompts (“push bombing”), hijacking phone numbers through SIM-swap attacks, and impersonating IT help desk staff to steal credentials. Once inside, they use “everyday” administrative tools and legitimate remote access applications to move quietly through networks, steal sensitive data, and in many cases deploy ransomware such as DragonForce [1, 2]. Scattered Spider is a serious concern because they adapt quickly, move across multiple industries, and combine human manipulation with technical persistence. [2, 7]
In today’s fast-paced technological and cybersecurity environment, staying ahead of the game is critical, and members of the Scattered Spider understand this well. They take advantage of the newest technologies, quickly identifying vulnerable areas and exploiting them for attack. For this reason, they have gained reputation as one of the most dangerous threat groups active today.
This report will outline who they target, the tactics they use, indicators of compromise, and how different roles can defend against them.
II. Target
Scattered Spider’s targets span across multiple industries, with the most recent being retail, insurance companies, and aviation. These incidents have impacted many countries worldwide and are most heavily hit in the U.S. and U.K. They go after large companies exploiting help desks and compromising third-party vendors such as customer support platforms, IT contractors, or cloud services. The following examples highlight major attacks between April and July 2025.
- April 2025
- Marks and Spencer (Retail, U.K.) – Struck by a ransomware attack that disrupted operations, cut into sales, and exposed customer and employee data. Attackers gained access through social engineering that targeted IT help desks, a tactic characteristic of Scattered Spider [3].
- Co-op (Retail, U.K.) – Experienced ransomware attacks causing data loss and service outages, negatively affecting company revenue and stock. Investigators revealed that access was granted through the impersonation of support staff and later passed to a ransomware-as-a-service (RaaS) operator, methods closely matching Scattered Spider’s standard techniques [4].
- May 2025
- Victoria’s Secret (Retail, U.S.) – Forced to shut down their website and in-store services following a security breach that was part of a wider campaign targeting retail [5].
- Adidas (Retail, Germany, global) – Confirmed theft of company and customer contact information through a third-party customer service provider [6].
- June 2025
- AFLAC (Insurance, U.S.) – Confirmed a data breach with Scattered Spider’s use of social engineering suspected for initial access.
- Philadelphia Indemnity Insurance (Insurance, U.S.) – Suffered a data breach linked to Scattered Spider’s use of Multi-Factor-Authentication (MFA) fatigue attacks.
- WestJet (Aviation, Canada) – Data centers breached along with their Microsoft Cloud environment. Scattered Spider gained their initial access through password reset on an employee account and using MFA to gain further access.
- Hawaiian Airlines (Aviation, U.S.) – Believed to have also been attacked by Scattered Spider, although investigations are ongoing and see similarities in tactics to other airline attacks.
- July 2025
- Qantas (Aviation, Australia) – Suffered significant data breach through a third-party customer service platform affecting nearly 6 million customers. Members of the Scattered Spider are believed to be responsible through targeting an IT call center.
- Azpiral (Loyalty Program Provider, U.K.) – Loyalty program provider for Co-op UK, disclosed a cyberattack extending impact beyond the retail company itself [7].
III. Tactics and Techniques
Scattered Spider incorporates a wide range of Tactics, Techniques, and Procedures (TTPs) to get what they want. They consistently rely on social engineering, most commonly impersonation of IT or Helpdesk personnel to deceive employees into revealing credentials, approving MFA prompts, or granting remote access.
The following list shows their tactics and techniques, along with the corresponding MITRE ATT&CK technique IDs.
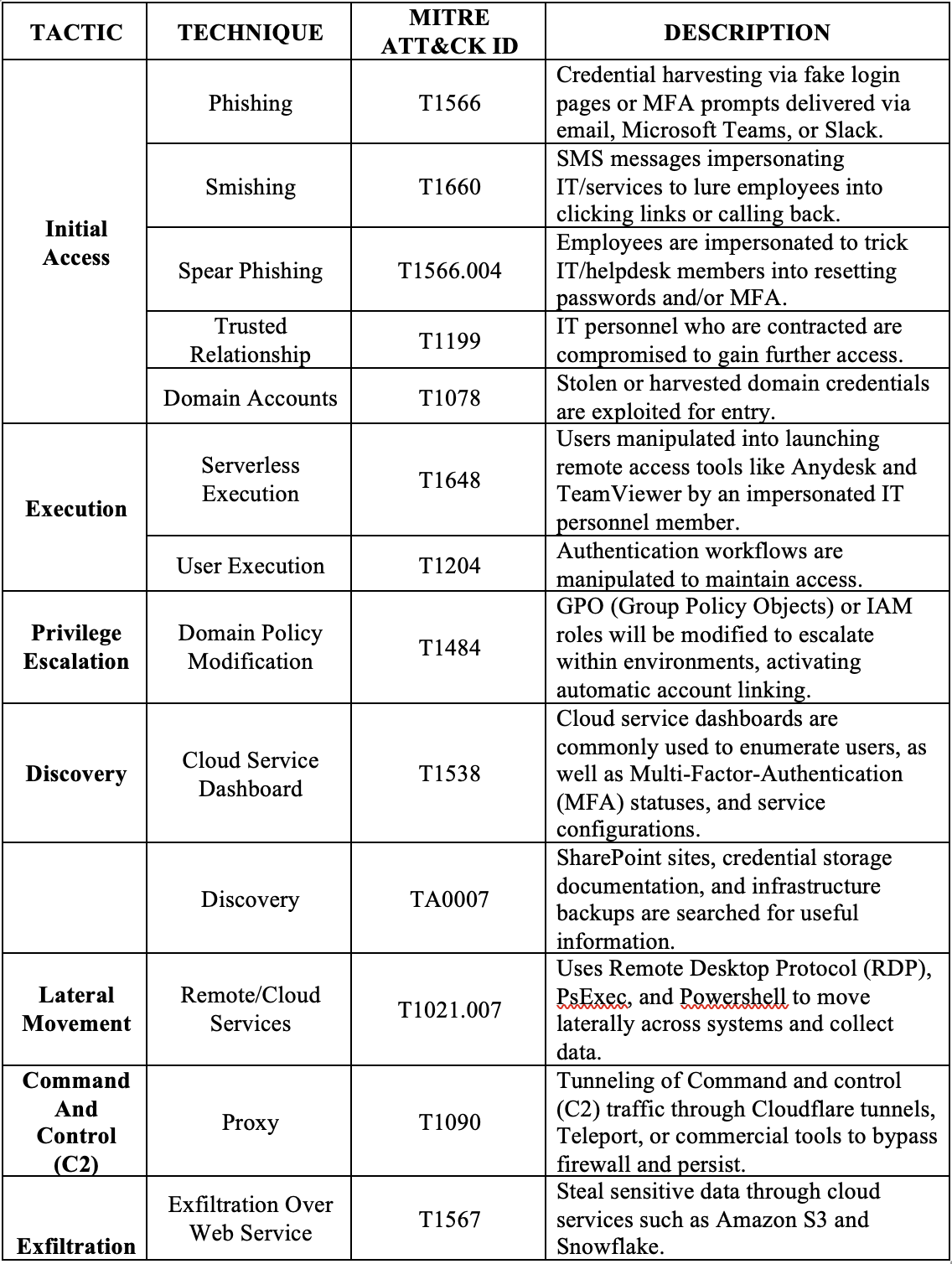
IV. Adversary Tools and Services
Scattered Spider relies on social engineering and trusted IT tools rather than custom malware. This helps them stay undiscovered in corporate environments [4].
Based on the recently published reports by CISA (2025) and CrowdStrike (2025), they use the following tools and services to maintain their persistence in the compromised systems:
- Remote Access Tools: AnyDesk, TeamViewer, Teleport.sh, and ScreenConnect provide persistent remote connectivity by tunneling over the internet [1].
- Cloudflare Tunnels: Cloudflare’s trycloudflare creates encrypted tunnels that bypass company firewalls and VPNs without raising suspicion. [9].
- Communication Platforms: Slack, Microsoft Teams and even SMS platforms would be exploited for social engineering, impersonating IT staff and targeting privileged users [9].
- Cloud Storage and Databases: Mega.nz, and Amazon S3, and Snowflake are mishandled for large-scale data exfiltration. Thousands of rapid queries would be used to pull out huge amounts of data in a very short time [9].
- Living off the Land Tools: PsExec, Powershell and Remote Desktop Protocol (RDP) allows for stealthy command execution, credential theft, and lateral movement disguised as routine I activity [9, 10].
- Malware and Ransomware (less common): AveMaria/WareZone (RAT), Racoon and Vidar (stealers), and ALPHV/BlackCat or DragonForce (ransomware) are deployed occasionally for persistence, theft, and extortion [1, 12].
V. Indicators of Compromise (IOCs)
Because Scattered Spider is known for blending in with legitimate user activity, this makes spotting them challenging. To stay ahead of them, defenders should look for subtle anomalies that give away their presence rather than just the tools themselves [11]. These clues, when pieced together, can help identify an attack even before major damage is done.
1. Impersonation Domains: Fake login/helpdesk sites. These domains typically impersonate corporate login or IT helpdesk pages, making them appear trustworthy to targets.
- In the past they have used: [1]
- targetsname-sso[.]com,
- targetsname-servicedesk[.]com,
- targetsname-okta[.]com,
- targetsname-helpdesk[.]com,
- oktalogin-targetcompany[.]com
2. Remote Access Abuse: Unexpected installation of remote access tools like AnyDesk, TeamViewer, Teleport.sh, and ScreenConnect (mentioned above) or unusual connections to unknown domains.
3. Tunneling Traffic: Repeated connections to trycloudflare domains that bypass VPN/firewalls.
4. Abnormal Data Exfiltration Patterns: Bursts of SQL queries executed against databases, large uploads to Mega.nz or Amazon S3 buckets outside of normal workflow [8], or high-volume outbound traffic from accounts or servers that don’t usually transfer large datasets.
5. Credential and Privilege Abuse: Repeated failed login attempts followed by successful access from a new or foreign IPs, unexpected privilege escalations or password resets, and MFA bypass attempts via helpdesk calls (vishing) or SIM swaps [13].
VI. Recommendations
Scattered Spider has impacted a wide range of individuals within targeted organizations by exploiting both human behavior and weaknesses in cloud identity systems. Their tactics allow them to compromise accounts across all levels of a company. Because their attacks touch so many different roles, a one-size-fits-all approach to mitigation would be insufficient.
This report breaks down mitigation strategies by role group, focusing on the four most frequently targeted groups: IT Support and Help Desk Personnel, Identity & Access Administrators, Executives & High-Privilege Users, and Standard Users across the Organization. Each section highlights who these groups are, how they are attacked, and what can be done to reduce the exposure to the attack, boosting resilience to a group whose playbook is to exfiltrate victims’ data and extort them for financial gain.
1. IT Support & Help Desk Personnel: Front-liners responsible for password resets, multi-factor authentication setup/resets, as well as employee account recovery. Scattered Spider targets this group the most by frequently impersonating employees calling IT support and Help desk personnel during after-hours (A time when not many people are around to verify legitimacy) requesting an “authentication reset” to gain remote access on that employee’s device.
How to Defend:
-
- Be trained in detecting social engineering, especially during after-hours or peak times when there are multiple requests in short windows.’
- Create a process that can be implemented for out of band authorization, meaning that if an employee calls saying they have lost their password and phone, be able to differentiate between a legitimate employee calling and a threat actor, like Scattered Spider, calling in to gain initial access.
- Log and audit all reset/MFA enrollment and reset requests.
- Block unauthorized Remote Monitoring and Management tools.
- Use fallback verification channels, such as alternate phone numbers, to confirm identity.
2. Identity & Access Management Administrators: Control who can log into systems and what they can access. IAM Administrators manage passwords, multi-factor authentication, cloud access, and application permissions. They essentially hold the keys to everything. If an attacker compromises an IAM account, they can access multiple systems, escalate privileges to gain even more control, disable protections like MFA, remain hidden longer, exfiltrate sensitive data, or launch larger attacks.
How to Defend:
- Have strong conditional access policies. Conditional access policies let you restrict logins to known IPs, managed devices, and geofenced locations, as well as specify token lifetimes to be short enough so even if it was stolen it will not work [14].
- Use stronger multi-factor authentication for admins, such as hardware-based tokens or NFC connections. Hardware tokens are highly resistant to phishing and are not reliant on mobile devices [15].
- Implement passkeys for employee authentication. Passkeys are cryptographic keys stored directly to a specific device and cannot be linked or synced to other devices [16].
- Don’t let admin access be “always on.” Give admin access only when necessary, not all the time. (This is also called “just-in-time” access.)
- Implement allow-listing and block known applications used by Scattered Spider and only allowing specific internal tools used within the company [17].
- Watch for suspicious activity. Flag whenever someone logs in from a new device or location, or if a login token gets reused.
- Clean up unused integrations. Disconnect old logins and apps that are no longer used, as they are an easy way to get in.
3. Executives & High-Privilege Users: Individuals with access to extremely valuable data, such as sensitive financial, legal, or insurance information. They are the prime targets for extortion and leveraging attacks due to having broader system privileges across the organization.
Why they are targeted: Offers high-value access with minimal friction. Executives often have direct access to confidential documents; their accounts typically have higher internal trust, and if compromised, could be used to trick others within the organization. Executive accounts are also often over-permissioned and interwoven in multiple high-risk systems, so one compromise can rapidly destruct laterally.
How to Defend:
- Be phishing savvy.
- Use hardware-based multi-factor authentication to prevent SIM-swaps and push bombing, a method used to overwhelm a user with repeated multi-factor authentication push notifications in hopes that the user will eventually approve out of annoyance.
4. Standard Users Across the Organization: Everybody else using email, SaaS (Software-As-A-Service, software solutions delivered over the internet on a subscription basis) apps, and cloud tools.
How they are targeted: Phishing, smishing, and multi-factor authentication attacks
How to Defend:
- Partake in ongoing training with phishing and smishing simulations and report suspicious MFA prompts.
- Use strong passwords, including no reuse, no hints, and use of password managers.
- Disable email-based onetime passwords as this can be leveraged to gain onwards authentication.
- Enable account lockouts after failed login attempts to limit brute-force access.
- Block unauthorized software, especially remote access or monitoring tools.
- Update devices and software regularly.
- Be cautious when uploading or sharing files in cloud platforms like SharePoint, Slack, or email.
VII. References
[1] Scattered spider: Cisa. Cybersecurity and Infrastructure Security Agency CISA. (2025, July 31). https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-320a
[2] Scattered spider. Scattered Spider, Roasted 0ktapus, Octo Tempest, Storm-0875, Group G1015 | MITRE ATT&CK®. (2024, April 4). https://attack.mitre.org/versions/v17/groups/G1015/
[3] Tidy, J. (2025, May 21). M&S and co-op hacks: Scattered spider is focus of police investigation. BBC News. https://www.bbc.com/news/articles/ckgnndrgxv3
[4] Poston, H. (2022, March 21). £300m gone: How scattered spider hit the UK’s biggest retailers. Hack The Box. https://www.hackthebox.com/blog/scattered-spider-insurance-retail-attacks
[5] Silberstein, N. (2025, June 13). Update: May cyber attack expected to cost victoria’s secret $20 million. Retail TouchPoints. https://www.retailtouchpoints.com/topics/security/data-security/victorias-secret-latest-hit-in-growing-swath-of-retail-cyber-attacks
[6] Beek, K. (2025, May 27). Adidas falls victim to third-party Data Breach. https://www.darkreading.com/vulnerabilities-threats/adidas-victim-third-party-data-breach
[7] Scattered spider targets tech companies for help-desk exploitation. ReliaQuest. (2025, June 23). https://reliaquest.com/blog/scattered-spider-cyber-attacks-using-phishing-social-engineering-2025/
[8] Fadilpašić, S. (2025, July 30). FBI, CISA warn of more scattered spider attacks to come. TechRadar. https://www.techradar.com/pro/security/fbi-cisa-warn-of-more-scattered-spider-attacks-to-come
[9] Scattered spider escalates attacks across industries. CrowdStrike. (n.d.). https://www.crowdstrike.com/en-us/blog/crowdstrike-services-observes-scattered-spider-escalate-attacks/
[10] Yasir, S. (2025, July 7). Inside the scattered Spider Attack: How a UK retail giant was breached and what it means for… Medium. https://medium.com/@shaheeryasirofficial/inside-the-scattered-spider-attack-how-a-uk-retail-giant-was-breached-and-what-it-means-for-e3e94a7ce5bf
[11] Richardson, J. (2025, July 29). Scattered spider: The looming shadow over U.S. cybersecurity. Medium. https://medium.com/@the-prototype/scattered-spider-the-looming-shadow-over-u-s-cybersecurity-e8ce141185a5
[12] Tahir. (2025, May 2). Unmasking the scattered Spider Threat actor. Medium. https://medium.com/@tahirbalarabe2/%EF%B8%8Funmasking-the-scattered-spider-threat-actor-6435c2439ed7
[13] Doyle, A., & Langley, M. (2025, June 9). Scattered spider: A web of social engineering – threat actors. Daily Security Review. https://dailysecurityreview.com/resources/threat-actors-resources/scattered-spider-a-web-of-social-engineering/
[14] Shastri, V. (2025, January 15). What is conditional access?. CrowdStrike. https://www.crowdstrike.com/en-us/cybersecurity-101/identity-protection/conditional-access/
[15] Horn, P. (2025, July 11). Passkeys vs Hardware Tokens: Phishing-resistant MFA. Accutive Security – The IAM + Crypto Products and Services Company. https://accutivesecurity.com/guide-to-passkeys-and-hardware-security-tokens-yubikeys/
[16] Passkeys: Passwordless authentication. FIDO Alliance. (2025, July 24). https://fidoalliance.org/passkeys/
[17] What is allowlisting?: Broadcom. Broadcom Inc. (n.d.). https://www.broadcom.com/topics/allowlisting
Threat Advisory created by The Cyber Florida Security Operations Center. Contributing Security Analysts: Waratchaya Luangphairin (June), Taylor Alvarez, Lara Radovanovic, Sneha Lama
To learn more about Cyber Florida visit: www.cyberflorida.org














