I. Targeted Entities
- MOVEit Customers
II. Introduction
A critical SQL injection vulnerability has been discovered in MOVEit, a managed file transfer software. Exploiting this flaw, remote attackers gained unauthorized access to the database, enabling them to execute arbitrary code.
III. Additional Background Information
The Cybersecurity & Infrastructure Security Agency has issued an alert about the use of a SQL injection vulnerability in the MOVEit Transfer web application, CVE-2023-34362. This could allow an unauthenticated attacker to gain access to MOVEit Transfer’s database. According to its development company Progress, an attacker may be able to infer information about the structure and contents of the database and execute SQL queries that alter or delete data, depending on the database engine that is being used, such as MySQL or Azure SQL (Progress). All versions of MOVEit Transfer are affected by this vulnerability (Pernet), and the exploitation of the MOVEit Transfer environment can occur via HTTP or HTTPS.
An unauthenticated, remote attacker could exploit this vulnerability by sending a specially crafted request to a vulnerable MOVEit Transfer instance (Tenable). On compromised systems, unauthorized access may appear as unexpected file creation in the MOVEit Transfer root folder c:MOVEit Transferwwwroot or appear similar to exfiltration traffic such as unexpected large file downloads and uploads (Kroll) from unknown IP addresses (Pernet).
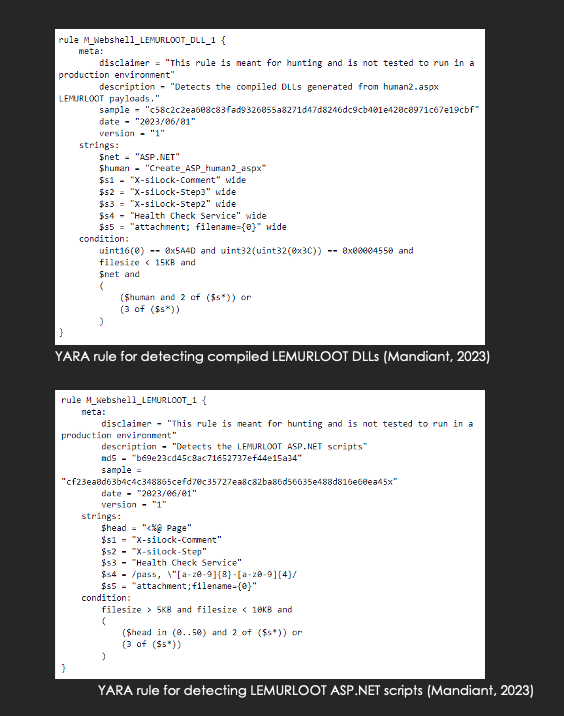
The threat actors deployed a LEMURLOOT web shell named human2.aspx located in the wwwroot folder of the MOVEit install folder. The file name has probably been chosen to remain unnoticed since another legitimate component of the software called human.aspx is used by MOVEit for its web interface. The web shell’s access is protected by a password. Attempts to connect to the web shell without the proper password results in the malicious code providing a 404 Not Found error (Pernet).
LEMURLOOT is written in C# and is designed to interact with the MOVEit Transfer environment. The malware can authenticate incoming connections using a hard-coded password and after successfully breaching into the system, it can run multiple commands and scripts from the X-siLock-Step1 – 3 fields that will download sensitive files from the MOVEit Transfer database, extract Azure system settings, retrieve detailed record information, create and insert a particular user, or delete this same user. Data returned to the system interacting with the LEMURLOOT web shell is gzip compressed (Mandiant)
The vulnerability is known to affect all versions of the MOVEit Transfer product with the earliest known exploitation dating to May 27, 2023 (Mandiant). Patches are available for all years of the MOVEit Transfer product. Currently, other MOVEit products such as MOVEit Automation, Client, Mobile, Gateway, etc. are not susceptible to vulnerability and do not require any immediate action (Progress).
IV. MITRE ATT&CK
- T1190 – Exploit Public Facing Application
Adversaries may attempt to exploit a weakness in an Internet-facing host or system to initially access a network. The weakness in the system can be a software bug, a temporary glitch, or a misconfiguration. Exploited applications are often websites/web servers, but can also include databases (like SQL), standard services (like SMB or SSH), network device administration and management protocols (like SNMP and Smart Install), and any other system with Internet-accessible open sockets. Depending on the flaw being exploited this may also involve Exploitation for Defense Evasion. - T1059.001 – Command and Scripting Interpreter: PowerShell
Adversaries may abuse PowerShell commands and scripts for execution. PowerShell is a powerful interactive command-line interface and scripting environment included in the Windows operating system. Adversaries can use PowerShell to perform a number of actions, including discovery of information and execution of code. Examples include the Start-Process cmdlet which can be used to run an executable and the Invoke-Command cmdlet which runs a command locally or on a remote computer (though administrator permissions are required to use PowerShell to connect to remote systems). - T1059.003 – Server Software Component: Web Shell
Adversaries may backdoor web servers with web shells to establish persistent access to systems. A Web shell is a Web script placed on an openly accessible Web server to allow an adversary to use the Web server as a gateway into a network. A Web shell may provide a set of functions to execute or a command-line interface on the system that hosts the Web server.
- T1210 – Exploitation of Remote Services
Adversaries may exploit remote services to gain unauthorized access to internal systems once inside a network. Exploitation of a software vulnerability occurs when an adversary takes advantage of a programming error in a program, service, or within the operating system software or kernel privileges to execute adversary-controlled code. A common goal for post-compromise exploitation of remote services is for lateral movement to enable access to a remote system. An adversary may need to determine if the remote system is in a vulnerable state, which may be done through Network Service Discovery or other Discovery methods looking for common, vulnerable software that may be deployed in the network, the lack of certain patches that may indicate vulnerabilities, or security software that may be used to detect or contain remote exploitation. Servers are likely a high value target for lateral movement exploitation, but endpoint systems may also be at risk if they provide an advantage or access to additional resources.
V. Recommendations
- Disable HTTP and HTTPS traffic to their MOVEit transfer Environment
- Check for indicators or unauthorized access in the last 30 days
- Apply patches as they become readily available
- Kroll advises MOVEit Administrators look in the “C:MOVEit Transferwwwroot” directory for suspicious .aspx files such as “human2.aspx” or “machine2.aspx”.
VI. IOCs (Indicators of Compromise)
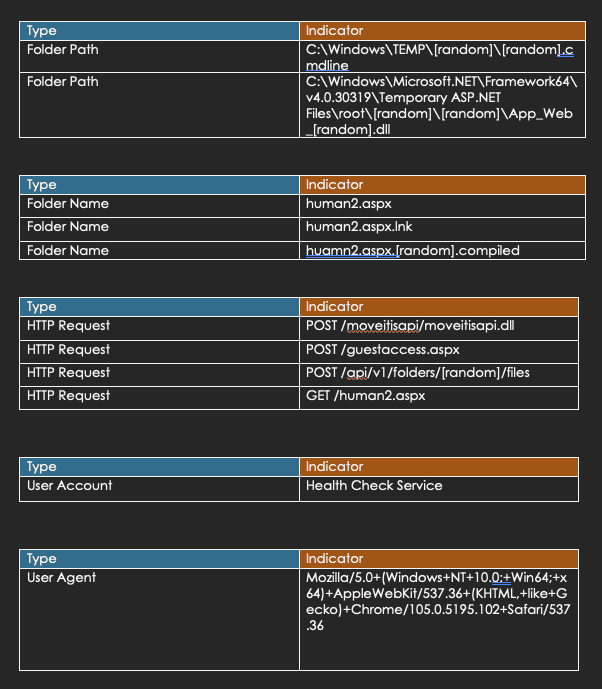
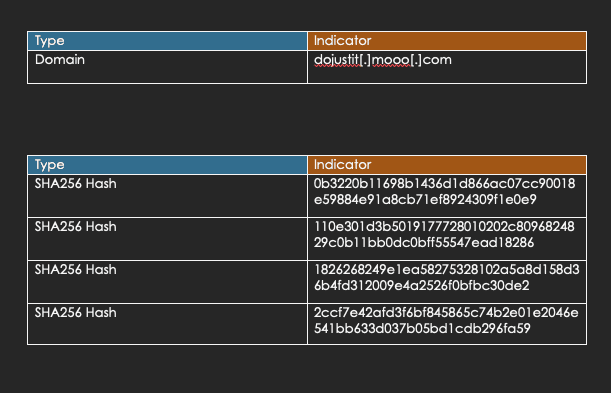
VII. Additional OSINT Information
VIII. References
Kroll. (2023, June 7). Critical MOVEit Transfer Vulnerability (CVE-2023-34362).
https://www.kroll.com/en/insights/publications/cyber/responding-critical-moveit-transfer-vulnerability-cve-2023-34362
Mandiant. (2023, June 2). Zero-Day Vulnerability in MOVEit Transfer Exploited for Data Theft.
https://www.mandiant.com/resources/blog/zero-day-moveit-data-theft
Pernet, C. (2023, June 6). Zero-day MOVEit Transfer vulnerability exploited in the wild, heavily targeting North America. TechRepublic.
https://www.techrepublic.com/article/zero-day-moveit-vulnerability/
Tenable®. (2023, June 2). CVE-2023-34362: MOVEIt Transfer Critical Zero-Day Vulnerability Exploited in the Wild.
https://www.tenable.com/blog/cve-2023-34362-moveit-transfer-critical-zero-day-vulnerability-exploited-in-the-wild
Progress Customer Community. (2023, June 16). Community.progress.com.
https://community.progress.com/s/article/MOVEit-Transfer-Critical-Vulnerability-31May2023
Threat Advisory created by The Cyber Florida Security Operations Center. Contributing Security Analysts: EJ Bulut, Benjamin Price, Erika Delvalle, Nahyan Jamil, and Alessandro Lovadina
