Volt Typhoon Attacks U.S. Critical Infrastructures Using LOTL Techniques

I. Targeted Entities
U.S. Critical Infrastructures
II. Introduction
CISA, NSA, and FBI have confirmed that Volt Typhoon has compromised the IT environments of multiple critical infrastructure organizations—primarily in Communications, Energy, Transportation Systems, and Water and Wastewater Systems Sectors—in the continental and non-continental U.S. and its territories, including Guam.
Volt Typhoon’s choice of targets and pattern of behavior is not consistent with traditional cyber espionage or intelligence gathering operations, and the U.S. authoring agencies assess with high confidence that Volt Typhoon actors are pre-positioning themselves on IT networks to enable lateral movement to OT assets to disrupt functions.
These actors could use their network access for disruptive effects in the event of potential geopolitical tensions and/or military conflicts. (Cybersecurity and Infrastructure Security Agency, 2024)
III. Additional Background Information
In December 2023, an operation disrupted a botnet comprising hundreds of U.S.-based small office/home office (SOHO) routers that were hijacked by state-sponsored hackers from the People’s Republic of China (PRC). The hackers, known to the private sector as “Volt Typhoon,” used privately-owned SOHO routers infected with the “KV Botnet” malware to conceal the PRC origin of further hacking activities directed against the U.S. and other foreign victims. These further hacking activities included a campaign targeting critical infrastructure organizations in the U.S. and elsewhere that was the subject of a May 2023 FBI, National Security Agency, and CISA advisory (Office of Public Affairs, 2024).
The KV Botnet primarily targets Cisco and Net Gear routers, exploiting a vulnerability due to their “end of service” status. This means they were no longer receiving security patches or software updates from the manufacturer. The operation deleted the KV Botnet malware from the routers and took additional steps to sever their connection to the botnet, such as blocking communications with other devices used to control the botnet (Office of Public Affairs, 2024).
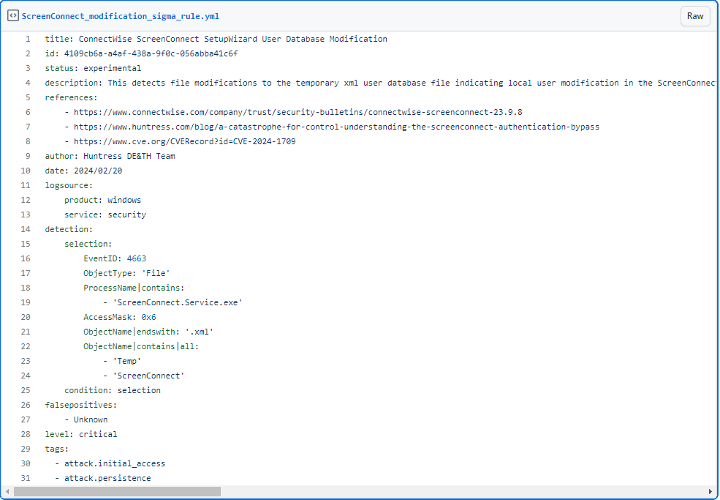
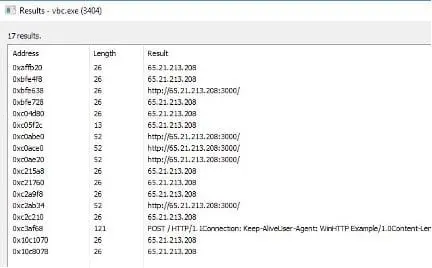
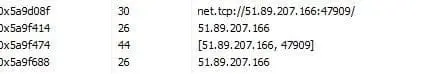
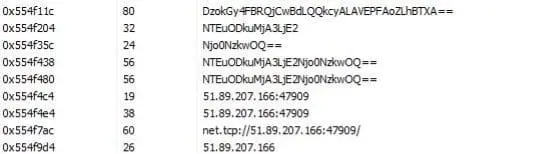
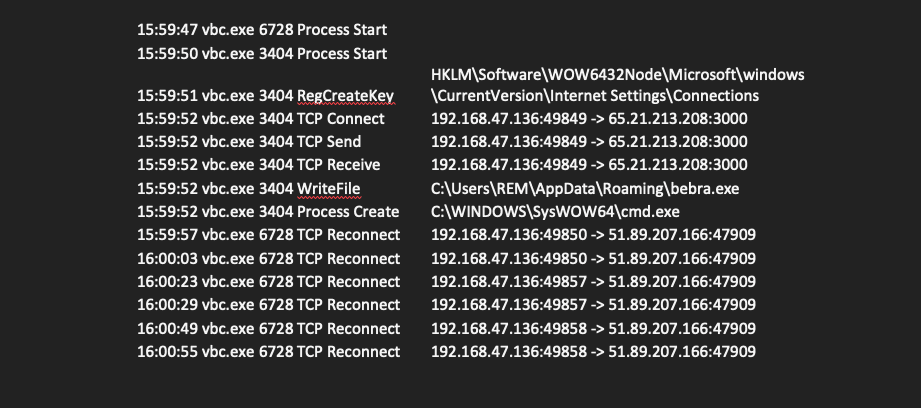
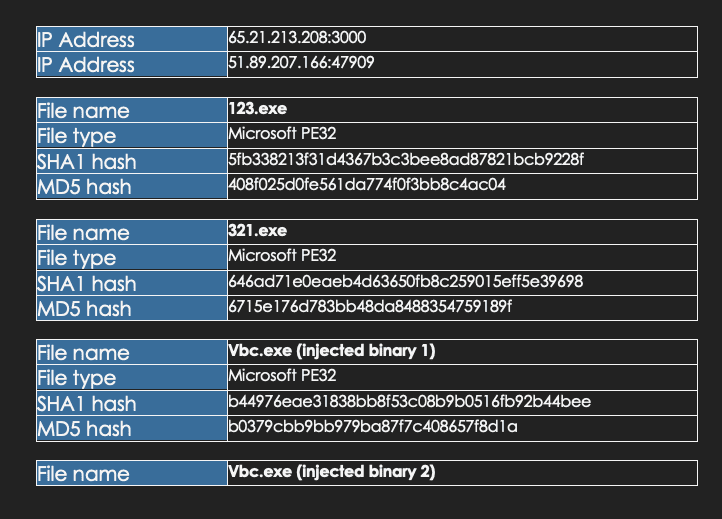
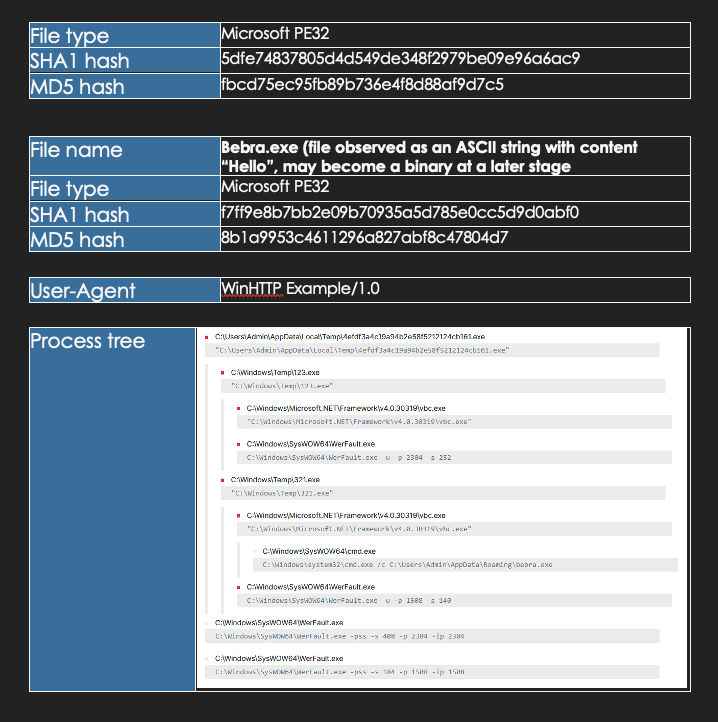
Volt Typhoon employs a multi-faceted approach to infiltrate and compromise target networks, starting with comprehensive pre-compromise reconnaissance to understand the network architecture and operational protocols. They exploit vulnerabilities in public-facing network appliances to gain initial access, then aim to escalate privileges within the network, often targeting administrator credentials. Utilizing valid credentials, they move laterally through the network, leveraging remote access services like Remote Desktop Protocol (RDP) to reach critical devices such as domain controllers (DC). Volt Typhoon conducts discovery within the network, utilizing stealthy tactics such as living-off-the-land (LOTL) binaries and PowerShell queries on event logs to extract critical information while minimizing detection. LOTL tools like ntdsutil, netsh, and systeminfo were used to gather information about the network service and system details. Also, Volt Typhoon implanted binary files such as SMSvcService.exe and Brightmetricagent.exe that can open reverse proxies between a compromised device and malicious C2 servers. The PowerShell script logins.ps1 was also observed collecting successful logon events on infected systems without being noticed. (Cybersecurity and Infrastructure Security Agency, 2024).
After achieving full domain compromise, Volt Typhoon extracts the Active Directory database (NTDS.dit) from the DC using techniques like the Volume Shadow Copy Service (VSS), bypassing file locking mechanisms. Additionally, Volt Typhoon uses offline password cracking methods to decipher hashed passwords, enabling elevated access within the network. With elevated credentials, Volt Typhoon focuses on strategic network infiltration, aiming to access Operational Technology (OT) assets, such as sensors and control systems. Volt Typhoon was observed testing access to OT systems using default vendor credentials and exploiting compromised credentials obtained through NTDS.dit theft. This access grants them the capability to potentially disrupt critical infrastructure systems such as HVAC and energy controls, indicating a significant threat to infrastructure security (Cybersecurity and Infrastructure Security Agency, 2024).
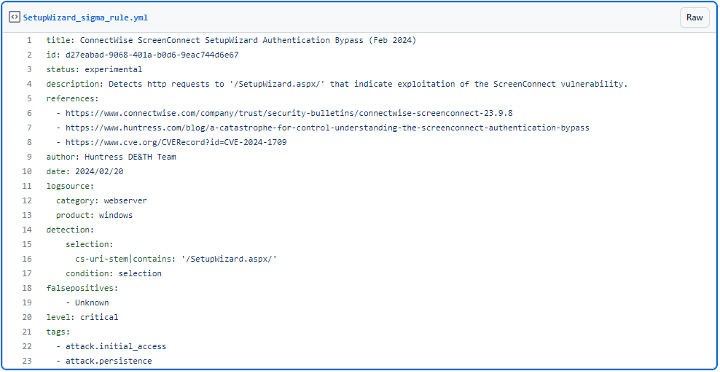
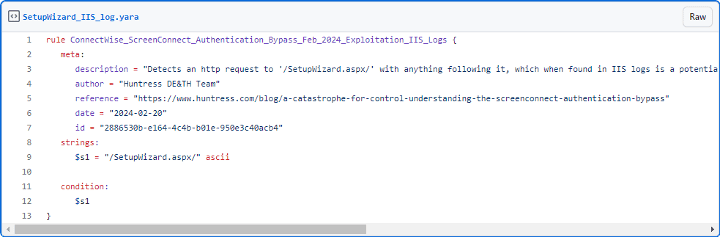
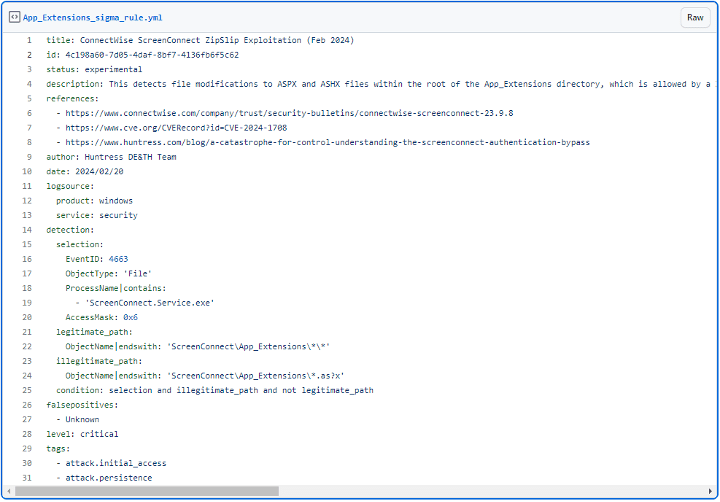
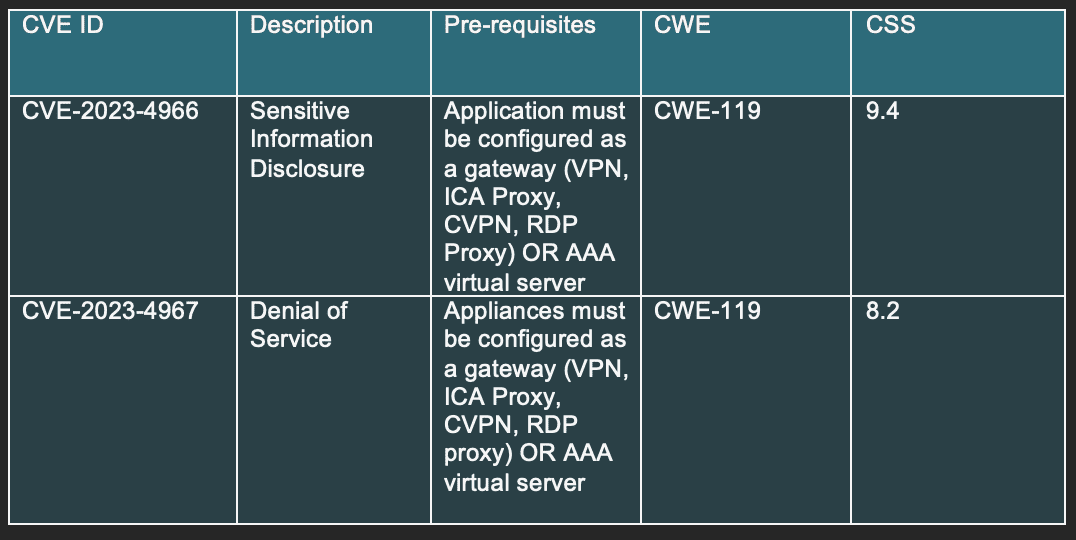
The second vulnerability, CVE-2024-1708, is related to CWE-22 – Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’). Although it is considered less severe as it is unlocked by CVE-2024-1079, it must not be underestimated (Team Huntress, 2024). This vulnerability involves manipulating ZIP file paths when extracting its contents. Attackers can then modify these contents and execute malicious code (Poudel, 2024). To do this, a malicious actor needs to have both administrative credentials and create a malicious extension inside C:Program Files (x86)ScreenConnectApp_Extensions to write files anywhere within the folder (Team Huntress, 2024). Team Huntress showed that this ZipSlip attack was not necessary, as malicious actors can run code by accessing a ScreenConnect feature called “Extensions”. This could potentially go easily unnoticed in a system since no other extensions need to be installed (Team Huntress, 2024).
ConnectWise released a patched version of ScreenConnect on February 21st, 2024, and recommends updating all 23.9.7 and earlier versions to 23.9.8 (ConnectWise, 2024). As of today, February 22nd, 2024, 3,800 instances of ScreenConnect have been found vulnerable, and need to be updated to the latest version in order to prevent malicious actors from accessing the ScreenConnect environment. ConnectWise added that Cloud instances were automatically patched, while On-Prem partners need to install all the required updates manually to remediate against both vulnerabilities (ConnectWise).
IV. MITRE ATT&CK
- T1592 – Gather Victim Host Information
Adversaries may obtain crucial details about victim hosts, encompassing administrative data (e.g., name, assigned IP) and configuration specifics (e.g., operating system). This information is gathered through various methods, including direct actions like Active Scanning or Phishing, as well as compromising sites to collect data from visitors.
- T1583.003 – Acquire Infrastructure: Botnet
Adversaries may obtain compromised systems through purchasing, leasing, or renting botnets, which are networks of compromised systems. By utilizing these botnets, adversaries can orchestrate coordinated tasks, including subscribing to services like booter/stresser to launch large-scale activities such as Phishing or Distributed Denial of Service (DDoS) attacks.
- T1190 – Exploit Public-Facing Application
Adversaries may exploit weaknesses in internet-facing systems, targeting software bugs, glitches, or misconfigurations. This may involve websites, databases, standard services, or network protocols, potentially leading to compromise. Cloud-based or containerized applications could provide access to underlying infrastructure, cloud/container APIs, or exploitation of weak access management. Edge network infrastructure and appliances may also be targeted. Frameworks like OWASP and CWE can be used to identify common web vulnerabilities that adversaries may exploit.
- T1078 – Valid Accounts
Adversaries leverage compromised credentials for various purposes such as Initial Access, Persistence, Privilege Escalation, or Defense Evasion. These credentials can circumvent access controls for resources, provide persistent access to remote systems, and access services like VPNs or Outlook Web Access. Adversaries often opt for legitimate access to evade detection, and inactive accounts may be exploited to avoid detection. The overlap of permissions across systems poses a risk, allowing adversaries to pivot and attain high-level access, bypassing enterprise controls.
- T1068 – Exploitation for Privilege Escalation
Adversaries may exploit software vulnerabilities to elevate privileges, capitalizing on programming errors in operating systems or kernel code to execute adversary-controlled actions. When operating with lower privileges, adversaries target higher-privileged components to escalate access, potentially reaching SYSTEM or root permissions. By exploiting vulnerabilities in drivers, adversaries may introduce a Bring Your Own Vulnerable Driver (BYOVD) for kernel mode code execution. - T1110.002 – Brute Force: Password Cracking
Adversaries use password cracking techniques to recover usable credentials, especially plaintext passwords, when they obtain credential material like password hashes. Techniques like OS Credential Dumping and Data from Configuration Repository can provide hashed credentials. Adversaries may systematically guess passwords or use pre-computed rainbow tables outside the target network to crack hashes, obtaining plaintext passwords for unauthorized access.
- Other Relevant MITRE ATT&CK Techniques
T1133, T1059, T1587.004, T1589, T1590, T1591, T1593.
V. Recommendations
- Apply patches
Prioritize patching key assets, known exploited vulnerabilities, and vulnerabilities in appliances frequently exploited by Volt Typhoon, such as Fortinet, Ivanti, NETGEAR, Citrix, and Cisco devices.
- Limit internet exposure of systems
An infrastructure’s primary attack surface is the combination of the exposure to all its internet-facing systems. One way to decrease the likelihood of a Volt Typhoon attack is to not expose systems to the internet when not necessary.
- Secure credentials and sensitive data
Ensure edge devices do not contain accounts or plaintext credentials that could provide admin access and ensure that only authenticated and authorized users can access the data.
- Implement MFA and the principle of least privilege
Make sure that MFA is enabled for every account and ensure administrator accounts only have the minimum permissions.
- Secure remote access services
Limit the use of RDP and other remote desktop services. If RDP is necessary, apply best practices, including auditing the network for systems using RDP, closing unused RDP ports, and logging RDP login attempts.
- Implement network segmentation
This practice can minimize the risk of lateral movement within networks, prevent and limit unauthorized access across domain boundaries, and isolate servers from other systems.
- Secure cloud assets
Revoke unnecessary public access to the cloud environment by ensuring that services such as storage accounts, databases, and VMs are not publicly accessible unless necessary.
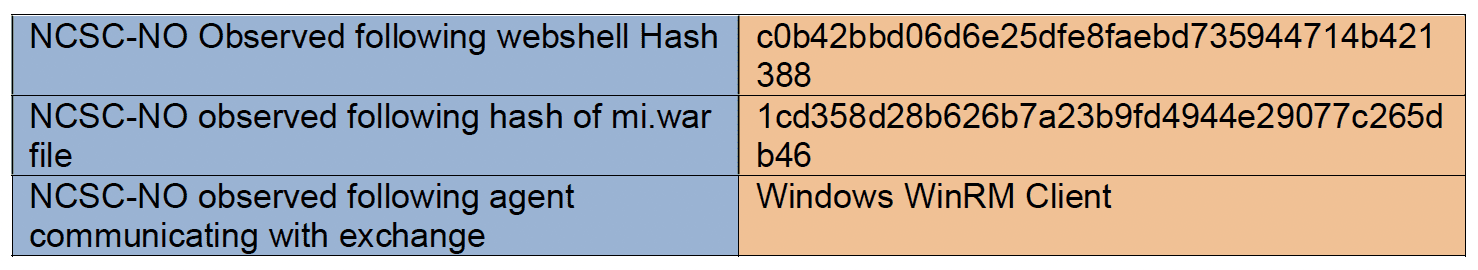
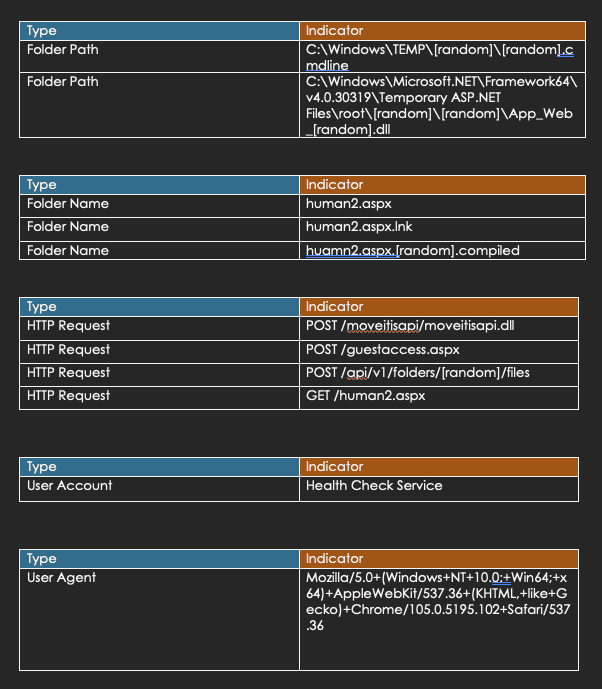
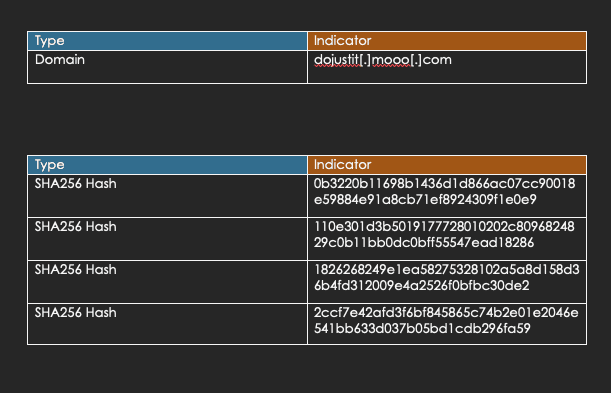
VII. IOCs (Indicators of Compromise)
CVE-2024-1709
| Type | Indicator |
|---|---|
| PowerShell Script |
C:{redacted}logins.ps1 |
| Folder Path |
C:UsersPublicpro |
| Folder Path |
C:WindowsTemptmpActive Directoryntds.jfm |
| Folder Path |
C:WindowsTemptmpActive Directoryntds.dit |
| Folder Path |
C:UsersPublicDocumentssysteminfo.dat |
| Folder Path |
C:UsersPublicDocumentsuser.dat |
| Folder Path |
Folder Path C:Users{redacted}DownloadsHistory.zip |
| Folder Path |
C:WindowsSystem32rult3uil.log |
| File Name |
comsvcs.dll |
| File Name |
NTDS.dit |
|
File Name |
SMSvcService.exe |
|
File Name |
Brightmetricagent.exe |
|
SHA256 Hash |
edc0c63065e88ec96197c8d7a40662a15a812a9583dc6c82b 18ecd7e43b13b70 |
|
SHA256 Hash |
99b80c5ac352081a64129772ed5e1543d94cad708ba2adc4 6dc4ab7a0bd563f1 |
VII. References
PRC State-Sponsored Actors Compromise and Maintain Persistent Access to U.S. Critical Infrastructure | Cybersecurity and Infrastructure Security Agency CISA. (2024, February 7). https://www.cisa.gov/news-events/cybersecurity-advisories/aa24038a#_Appendix_C:_MITRE
U.S. government disrupts botnet people’s republic of China used to conceal hacking of critical infrastructure. Office of Public Affairs | United States Department of Justice. (2024, January 31). https://www.justice.gov/opa/pr/us-government-disrupts-botnet-peoples-republic-china-used-conceal-hacking-critical
Threat Advisory created by The Cyber Florida Security Operations Center. Contributing Security Analysts: Alessandro Lovadina, Joy Boddu, Likhitha Duggi